The frequency of cyber-attacks has increased by 67% in the past five years. This significant increase underscores the growing threat landscape and the importance of staying vigilant and continuously updating cybersecurity defences.
What if a system outage or ransomware attack hit your business? Could you rebuild trust and recover financially?
Cybersecurity in 2024 isn’t about fear—it’s about being smart and prepared, like wearing a seatbelt. Threats evolve rapidly, but understanding how they work and how to protect yourself ensures you stay ahead. Ready to dive in and safeguard your digital future? Let’s begin.
The 6 most common cyber threats—and how to protect yourself
Forget trawling the dozens of research reports. We’ve done that for you and distilled the top six threats that re-emerge again and again.
1. The Digital Kidnapper: Ransomware
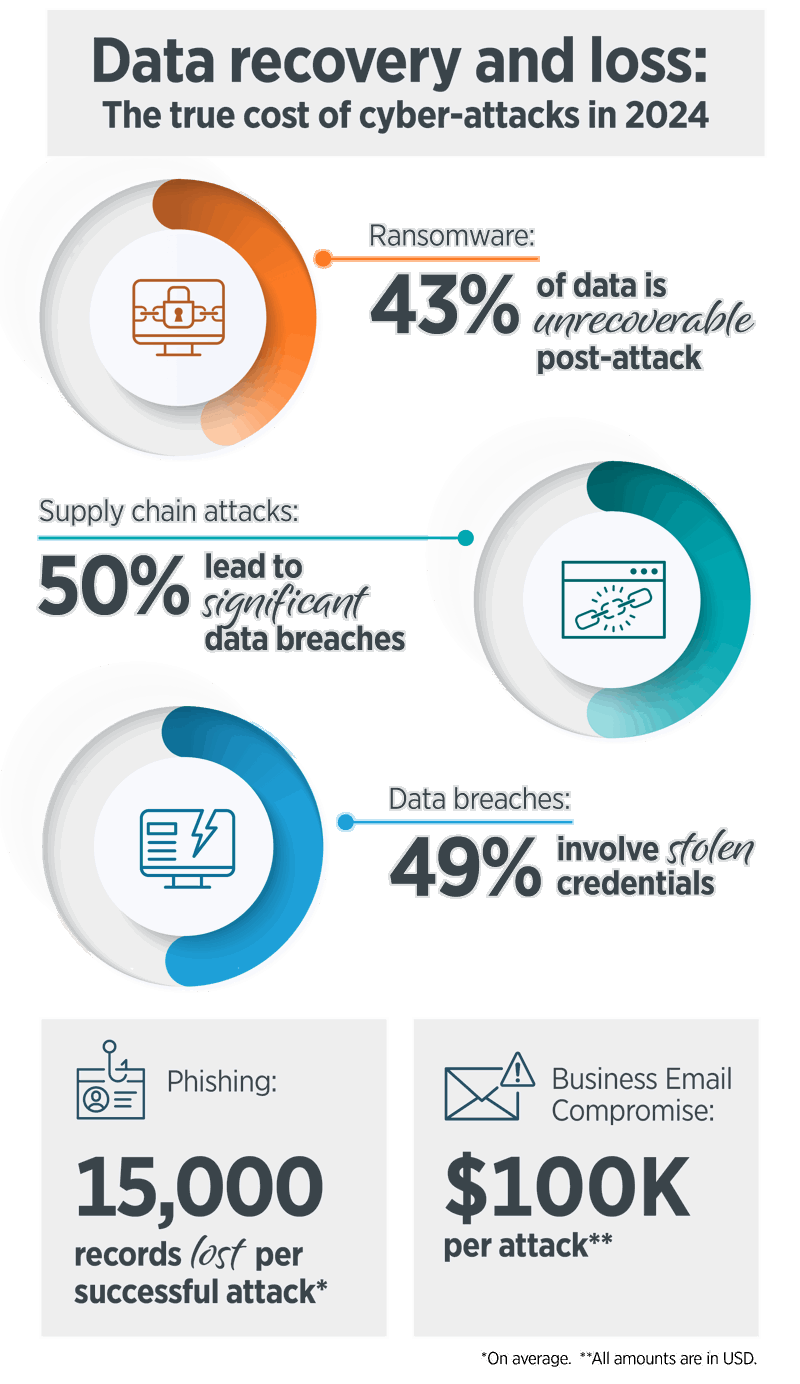
Imagine someone breaking into your house, locking all your valuables in a box, and demanding money to give you the key. That's what ransomware does, but to your digital world. It locks your important files and asks for money to unlock them. With the rise of Ransomware-as-a-Service, launching these attacks has become easier than ever, making it accessible to a wider range of cybercriminals.
Why it matters: Even if you pay, there's no guarantee you'll get your files back. Plus, it can cost businesses millions, which can affect jobs and services.
Your seatbelt: Always back up your important files on an external drive or a secure cloud service.

2. A hole in my bucket: Data breaches
A data breach happens when hackers break into a system and steal sensitive information like passwords, credit card numbers, or personal details.
Why it matters: This stolen information can be used for identity theft, fraud, and other malicious activities.
Your seatbelt: Use strong, unique passwords for different accounts and enable two-factor authentication.
3. Captain Baited Hook: Phishing
Phishing is like a trick email or message that pretends to be from someone you trust, like your bank or a friend, to steal your personal information. It often looks very convincing and asks you to click a link or provide details.
Why it matters: Falling for these tricks can lead to identity theft, financial loss, and more.
Your seatbelt: Be suspicious of unsolicited emails or messages asking for personal information. Verify by contacting the person or company directly using known safe contact information. If you don’t have this, refer to details published on the company’s official website. And as an organisation, implement robust and regular employee training.
4. Mistique: Business Email Compromise (BEC)
BEC is when a hacker pretends to be a high-ranking executive or trusted employee in a company to trick others into transferring money or sensitive information.
Why it matters: These attacks can result in substantial financial losses and data breaches. With advancements in deepfake technology, attackers can now simulate both voice and face with minimal audio samples, making these deceptions even more convincing.
Your seatbelt: Encourage staff to trust their instincts—if something feels off, they should terminate the suspicious communication immediately and initiate a new conversation via a verified phone number or in person. Always double-check email addresses and verify any unusual requests independently.
5. Robot: Identity-based attacks
These attacks focus on stealing and using your digital identity to gain unauthorised access to systems and data. Think of it as someone stealing your driver's license to impersonate you.
Why it matters: It can lead to unauthorised transactions, damage to your reputation, and long-term financial and legal issues.
Your seatbelt: Regularly monitor your bank statements and credit reports for unusual activity.
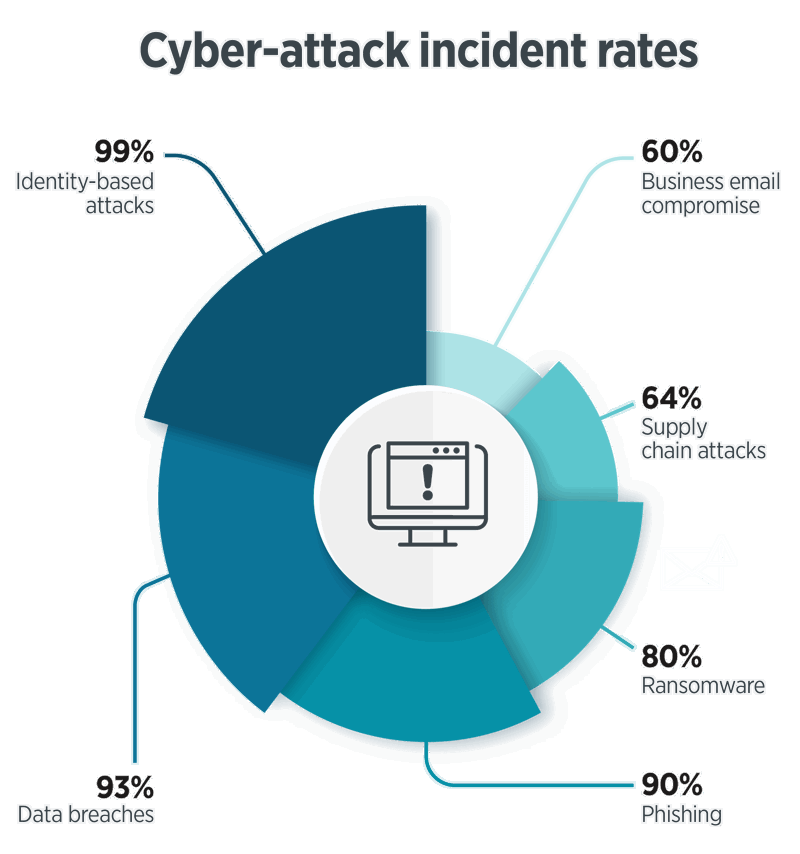
6. The Trojan Horse: Supply chain attacks
Supply chain attacks are like a Trojan horse. Hackers infiltrate software or hardware through a trusted vendor to spread malware or steal data.
Why it matters: These attacks can disrupt services, compromise data, and spread malware to many users.
Your seatbelt: Ensure your vendors follow strict cybersecurity practices and regularly update their systems.
Why cybersecurity is everyone’s responsibility
Cyber-attacks are not just a passing threat; they're becoming more sophisticated and as common as catching a cold. To effectively combat these threats, it's crucial to understand the what, why, how, and when of cyber-attacks. This knowledge can help slow down and even prevent the perpetrators behind them. The financial and operational implications of a cyber-attack can seem unfathomable and often intangible, which makes it challenging for organisations to prioritise their cybersecurity investments effectively.
Many attacks start with common entry points like phishing or stolen credentials, underscoring the need for defences that address these vulnerabilities head-on. Investing in robust cybersecurity measures is not just a technical necessity; it's a strategic imperative to safeguard your business's future.
Build a strong cybersecurity defence strategy
When it comes to defending your business against cyber threats, having a robust strategy is essential. First and foremost, it's crucial to implement comprehensive data visibility and management across all environments, whether on-premises, private, or public clouds. This visibility ensures you know exactly what's happening across your entire digital landscape. Additionally, adopting a layered defence strategy that includes prevention, detection, and response is vital. This means having visibility at all entry points and using advanced detection systems to monitor for stealthy activities.
Leveraging AI technology can significantly enhance your detection and response capabilities by automating these processes, but it's equally important to ensure your AI initiatives are securely implemented. Trust no one blindly, not even your CEO. Implementing robust identity access management solutions, including multi-factor authentication (MFA), role-based access controls, and continuous monitoring of user activity, is essential to safeguard critical systems and data.
Lastly, continuous improvement through regular staff training is key. Your team needs to understand the important role they play in cybersecurity and how to identify potential issues. By focusing on these strategies, you can build a resilient defence against the ever-evolving landscape of cyber threats.
Reference list:
- Checkpoint. (2024). 2024 Cyber Security Blog. Retrieved from Checkpoint: https://www.checkpoint.com/resources/report-3854/2024-cyber-security-report
- Gartner. (2024). Top Trends in Cybersecurity for 2024. Gartner. Retrieved from Gartner: https://www.gartner.com/en/cybersecurity/topics/cybersecurity-trends
- Brooks, C. (2024). Alarming Cybersecurity Stats: What You Need To Know In 2024. Forbes. Retrieved from Forbes: https://www.forbes.com/sites/chuckbrooks/2024/06/05/alarming-cybersecurity-stats-what-you-need-to-know-in-2024/
- IBM Security. (2024). Cost of a Data Breach Report 2024. IBM Security. Retrieved from IBM Security: https://www.ibm.com/reports/data-breach
- Secureworks. (2023). State of the Threat Report 2023. Secureworks. Retrieved from Secureworks: https://www.secureworks.com/resources/rp-state-of-the-threat-2023
- Deloitte. (2024). Annual Cyber Threat Trends 2024. Deloitte. Retrieved from Deloitte: https://www2.deloitte.com/us/en/pages/risk/articles/cybersecurity-threat-trends-report-2024.html
- CrowdStrike. (2024). State of Security 2024. CrowdStrike. Retrieved from Crowdstrike: https://go.crowdstrike.com/global-threat-report-2024.html
- Trend Micro. (2024). Top Cybersecurity Trends for 2024. Trend Micro. Retrieved from Trend Micro: https://www.trendmicro.com/en_gb/research/24/a/cybersecurity-trends-2024.html
- ConnectWise. (2024). 2024 MSP Threat Report. MSPAlliance. Retrieved from ConnectWise: https://www.connectwise.com/resources/2024-msp-threat-report
- SANS Institute. (2024). State of OT Cybersecurity 2024. SANS Institute. Retrieved from SANS Institute: https://www.sans.org/webcasts/sans-2024-ics-ot-survey-the-state-of-ics-ot-cybersecurity/
In this article





